Hashicorp Boundary Enterprise Activation key is a leading network infrastructure and access management solution designed to secure critical assets and sensitive environments. This comprehensive guide provides an in-depth look at Boundary Enterprise’s key capabilities, architecture, deployment options, and more.
- What is Download free Hashicorp Boundary Enterprise Activation key?
- Main Benefits and Use Cases of Free download Hashicorp Boundary Enterprise Activation key
- Key Features and Capabilities
- Hashicorp Boundary Enterprise Activation key Architecture Overview
- Implementation and Deployment Options
- Hashicorp Boundary Enterprise Pricing and Licensing
- Competitors and Alternative Solutions
- Conclusion and Summary
What is Download free Hashicorp Boundary Enterprise Activation key?
Hashicorp Boundary Enterprise Activation key is an enterprise-grade network perimeter security tool offered by HashiCorp. It helps secure cloud environments, data centers, and hybrid infrastructures by controlling access to critical resources and enforcing least privilege.
Key capabilities of Full version crack Hashicorp Boundary Enterprise Activation key include:
- Securing public cloud environments like AWS, Azure, and GCP
- Protecting Kubernetes clusters and containerized workloads
- Managing access to on-premises data centers and private clouds
- Integrating with identity providers for access controls
- Providing dynamic secrets management and credentials
- Limiting blast radius of breaches with microsegmentation
- Gaining visibility into all network flows between perimeter and resources
Hashicorp Boundary Enterprise Activation key uses an identity-based approach to enforce zero trust security. It verifies each connection attempt before granting the least privileged access needed. This minimizes attack surfaces and prevents lateral movement across environments.
Main Benefits and Use Cases of Free download Hashicorp Boundary Enterprise Activation key
Hashicorp Boundary Enterprise Activation key offers many benefits that make it a strong choice for securing modern IT environments:
Securing critical infrastructure – Boundary provides granular control and visibility for crown jewel environments like databases, proprietary apps, CI/CD pipelines, and more.
Managing complex network policies at scale – Boundary makes it easy to manage and enforce network-level access policies across large, distributed environments with many users, apps, and microservices.
Enforcing least privilege access – Organizations can implement zero trust models by enforcing least privilege for each connection and request. This reduces risk.
Microsegmentation – Boundary allows organizations to divide monolithic apps and environments into isolated microsegments. This limits lateral movement in the event of a breach.
Reducing attack surface – Boundary proxies and funnels all traffic through a single ingress point, obscuring internal resources and minimizing possible attack vectors.
See also:
Adobe Creative Cloud Collection 2024 Keygen v19.12.2023 Full Free
Key Features and Capabilities
Hashicorp Boundary Enterprise Activation key includes robust features that set it apart from competitors:
- Identity-based access controls – Integrates with LDAP, OAuth, SAML providers to enable granular, attribute-based access policies.
- User and machine-based policies – Apply fine-grained rules based on users, groups, roles, device posture, and more.
- Least privilege controls – Only allow the exact access that is needed, limiting blast radius of any breach.
- Just-in-time dynamic secrets – Automatically rotateshort-lived credentials and certificates to reduce standing privileges.
- Protection for hybrid environments – Consistent security policies across on-prem, public cloud, containers, and legacy systems.
- Integration with Hashicorp Vault – Joint solution with Vault for secrets management and data encryption.
- Real-time monitoring and auditing – Visibility into all requests and activities for auditing requirements.
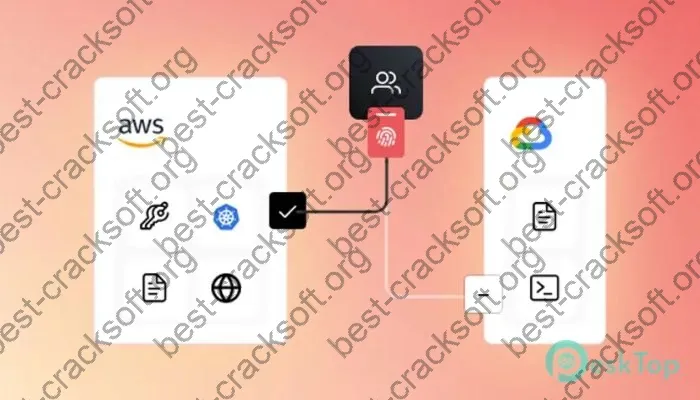
Hashicorp Boundary Enterprise Activation key Architecture Overview
Hashicorp Boundary Enterprise Activation key utilizes a multi-component architecture:
- Proxy – Single ingress point accepting all traffic and enforcing policies. Obscures internal resources.
- Controller – Centralized server that manages policies, security, and configurations.
- Worker – Distributed service that handles cryptographic tasks and secrets.
Together, these components establish a zero trust network perimeter to defend critical resources. The proxy brokers authorized connections while protecting against discovery of internal systems.
This allows organizations to reduce their attack surface drastically, grant least privilege access, and prevent lateral movement across environments.
Implementation and Deployment Options
Hashicorp Boundary Enterprise Activation key offers flexible implementation options:
- On-prem deployments – Can be deployed fully on-premises using provided virtual appliances.
- Public cloud deployments – Available via AWS, Azure, and GCP marketplaces for cloud-based usage.
- Hybrid models – Mixed environments are supported with consistent policies.
- Kubernetes integration – Deploy Boundary natively via Helm charts for protecting clusters.
- Terraform integration – Infrastructure-as-code deployments are possible using Terraform modules.
- Integration with cloud accounts – Policies can be tied to cloud provider identities and roles.
Boundary recommends deploying a minimum of 3 proxy instances for high availability along with at least 3 controllers and workers.
Hashicorp Boundary Enterprise Pricing and Licensing
Boundary Enterprise uses a tiered pricing model based on the number of “targets” secured:
| Plan | Price | Targets Secured |
|---|---|---|
| Starter | $15 per target per month | Up to 149 targets |
| Growth | $12 per target per month | 150-499 targets |
| Scale | $9 per target per month | 500+ targets |
Targets can be on-prem servers, cloud instances, container pods, users, service accounts, and more. Enterprise plans include premium support and features.
The free open source Boundary Server is available, but lacks enterprise capabilities like integrations, policies, and dashboard.
Competitors and Alternative Solutions
Key competitors to Free download Hashicorp Boundary Enterprise Activation key include:
- Cloudflare Access – Offers device and app access controls for SaaS and infrastructure.
- Perimeter 81 – Provides zero trust network access with a secure web gateway.
- Zscaler – Delivers cloud-based internet and web security solutions.
- Akamai Enterprise Application Access – Manages access to internal apps and resources.
However, Full version crack Hashicorp Boundary Enterprise Activation key stands apart with its focus on infrastructure and workload security, microsegmentation capabilities, DevOps integrations, and dynamic secrets management.
Conclusion and Summary
Hashicorp Boundary Enterprise Activation key enables organizations to securely connect anything to everything, while minimizing their attack surface drastically. With its identity-centric access controls, integration with secrets management, and support for hybrid infrastructure, Boundary is a robust tool for implementing zero trust and least privilege access models.
See also:
The speed is significantly faster compared to last year’s release.